Did you ever wonder how Facebook’s and Google’s ads are right on target – they are both mining your communications, the other cookies on your system that reveal where you have been and have been recording your conversations if Siri/Amazon Alexa/etc. are turned on and then subjecting all this to AI/machine learning analysis.
To illustrate this further, I recommend you have a look at your personal profile on Google (e.g. Google Ads Preferences). Now there are even emergent blackmailers that are mining user’s cookies and then blackmailing them by threatening disclosure of the sites the users have been to (See Ransomware). They then extend this with machine learning and predictive analytics and this will worsen as the IoT matures and reveals and adds “Dark Data” to the Big Data equation.
Profiling & Predictive Analytics Example
From the Colbert Report: Target’s marketing and predictive analytics which broke in a New York Times article… I apologize for his satirical humor as it is not for everyone but it is a very good presentation. Note the video is dated (e.g. 2012) and predictive analytics based on previously dark data and machine learning is advancing at a staggering rate.
Colbert’s Surrender to a Buyer Power
Now let’s recall what we have learned to date:
We have spoken about the fiscal benefits of the “Long Term Value or LTV” of consumers as it is is better to keep your existing customers than to continually seek new customers. Target clearly embraces this.
There are also ethics involved but recall ethical perspectives can be based on “Stockholder Theory”, “Stakeholder Theory” or “Social Contract Theory” so while we may not agree with Target’s or any organization’s use of publicly available information and predictive analytics they are simply doing what’s best for their stockholders… and on that note let’s continue.
Big Data & Predictive Analytics
Dr. Alessandro Acquisti of Carnegie Mellon University and brace yourself as its a new world… please consider both the positive and negative effects of this emergent information technology and also please keep in mind the business – IT – society triangle.
Now on this note, I highly recommend everyone take BADM 220 Statistics as this is the basis of both operational analytics (for everyday business efficiency) and predictive analytics for understanding and assessing trends, future events and risk assessment.
Now having watched this do you see any benefits of facial recognition… how about facial recognition at airports? I think the answer is absolutely but what about negative effects… what about the ability to see someone in a club, take their picture and immediately have their address and phone number or even facebook data like their previous relationships? Maybe even more concerning research China’s Social Credit system.
But it doesn’t end with pictures, what if someone posts something less than flattering on social media… this too will be available to prospective employers as they review your resume or even when they sit in front of you and interview you and ask questions. Also, know that employers increasingly use personality testing in the interview/hiring process. Have you or has anyone written anything about you on Facebook or Twitter or their like that can reveal personality traits… and remember it is a computer and its’ analytic algorithms that are doing the evaluation and profiling.
Now consider merging your social network data (that even includes what other people have written about you) and publicly available information as in the Ted Talks video above and the tracking and analytical profiling presented in the above Colbert “Surrendering to a Buyer Power) above and you have an even better understanding of individuals (if you haven’t done so, please Google “Google Ads Preferences” and see how well Google already profiles you).
He also mentioned that we may be offered the ability to manage this but that it is then taken away. Consider Google’s Internet capable Nest thermostat system that secretly included a microphone. When people identified that a microphone was in the system Google provided instructions to turn off the microphone but stated that consumers that turned off the microphone would be ineligible for security updates and customer support.
Let’s recall how I began the LM8 Security stating that security is 75% policy as Dr. Acquisti cite’s the need to formulate policy. He also references transparency and how many people just sign off on and continue using Facebook with each change to their privacy policy.
Ok, now consider the changes in Facebook’s privacy policy (or change to prevent privacy) and Google’s change in advertising to use your picture for your friends’ advertising… These changes took place on the same day but remember in accord with “Social Contract Theory” it’s a business decision.
Now recall my statement that if something is free, you or we are the product. Now let’s use our Business-IT-Society awareness and consider Windows 10… with its free upgrade… and facial recognition… and it cloud computing basis… and we can conclude that Microsoft is about to enter this arena… should we be worried about privacy?
China’s Social Credit System
Towards the end of the video you’ll learn about a Chinese journalist who was blacklisted (rights removed) when he tried to investigate corruption of senior politicians. Note this is just 1 video and there are many more YouTube videos on this and many journal articles.
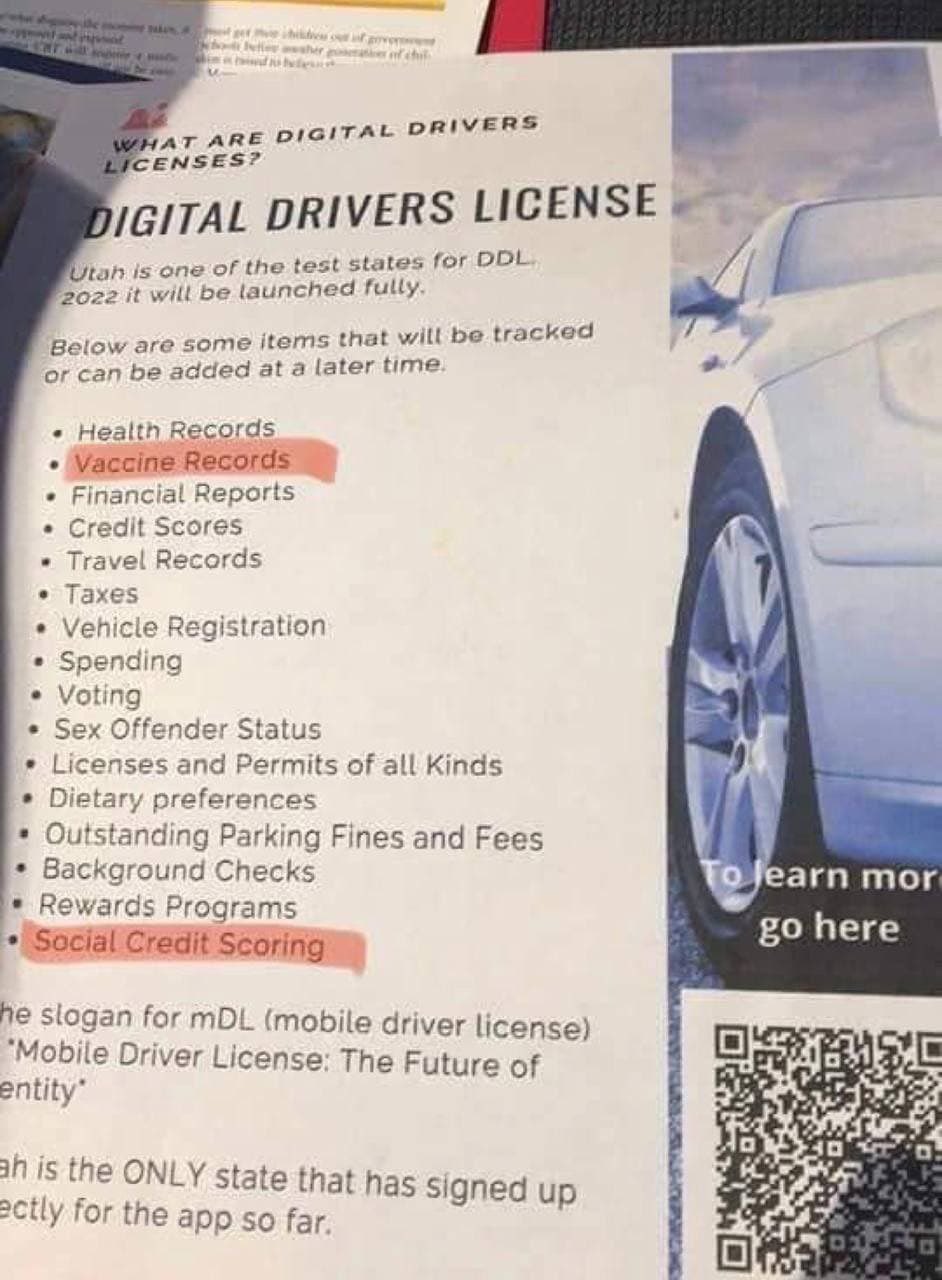
Now we think this could never occur in the US but consider Utah is piloting digital driver’s licenses that may contain vaccine status, social credit etc.
Why Privacy Matters
US Surveillance State
Example: What Google Knows About You
https://www.cnbc.com/video/2017/12/06/everything-google-knows-about-you.html
For unbiased search I recommend Duck Duck Go and the TOR or Brave browser
https://youtu.be/hIXhnWUmMvw?list=PLSVBzactXNXvEKzOixIrzNPJPeKage8kJ
Government Internet Surveillance
NSA
Email Privacy?
Generational change and information sharing. Consider our use of cloud-based email providers (gmail, hotmail, yahoo, etc.)
Now one of the previous videos presented cited Ed Snowden so let’s listen to Ed and hopefully heed his advice
Surveillance Under the Skin
What to do:
Well, Facebook, Twitter and the like are your choice. Beyond that, Chrome offers anonymous browsing by opening a “New Incognito Tab” and we know that another option is to use a distributed/anonymous network like TOR but the NSA can track either of these regardless. Other options as presented in class (or in videos) exist in the form of Chrome Plugins. As presented, I use Ghostery, DoNotTrack, and Disconnect to stop setting and mining of cookies. If a general user (like my mom) has to choose just one, I recommend disconnect as it also forces your browser to access the Secure https versions of Facebook, Google, etc. I also recommend the Do Not Track Plug-in as it may be the best as well (I have never performed the analysis).