Introduction
This presentation begins with a brief history of the Ethernet standard and its design considerations as this serves as a necessary foundation and puts the analysis in context. The analysis will proceed to describe the CSMA/CD protocol and its individual Carrier Sense, Collision Detect, and Collision Recovery components. Following this, we will proceed to analyze the Ethernet constraints and limitations imposed by the CSMA/CD protocol. The presentation will conclude with a description of the evolution of the Ethernet protocol to today’s switched Ethernet functionality that overcomes the shortcomings of legacy CSMA/CD implementations.
Ethernet
The Ethernet protocol was originally developed by Robert Metcalfe and his coworkers at Xerox in the 1970s. Metcalfe sought to benefit everyone by developing a cost-effective communications mechanism based on open standards that would provide efficient access to shared resources. Metcalf’s simple design stipulated a multi-access, contention-based linear bus. The first Ethernet standard was published in 1980 by the DIX consortium comprised of Digital Equipment Corporation (DEC), Intel and Xerox. As a result of this published standard, numerous products were quickly introduced and Ethernet was well on its way to becoming the de facto industry LAN standard.
Since 1985, Ethernet standards have been developed and set by the Institute of Electrical and Electronics Engineers (IEEE, 2009). One of the IEEE’s primary tenets was to keep the Ethernet standard compliant with the Open Systems Interconnection (OSI) model, therefore, maintaining its accessible design tenets. As a result, the IEEE 802.3 Ethernet protocols are implemented across the OSI data link layer and physical layers. The Ethernet standard further distinguishes the data link layer by dividing it into separate Logical Link Control (LLC) and Media Access Control (MAC) layers. The LLC is implemented in software and was designed to function independently from existing technologies thereby providing future-proof versatility to the network layers above it. In this capacity, the LLC serves as an intermediary between the IP layer and the data link’s MAC sub-layer. MAC is implemented in hardware, often in the form of a Network Interface Card (NIC) while the LLC’s software may be thought of as the driver for the NIC.
The original Ethernet standard specified a Carrier Sense Multiple Access with Collision Detection (CSMA/CD) access method for data communications (IEEE 802.3, 2009). Note the critical driving factor of Ethernet’s CSMA/CD protocol development and subsequent evolution described below is the multiple access communications medium. This shared medium allows all devices to access the communications medium whenever they have data to send however only one device can transmit at a time. This results in a contention-based environment where devices compete for bandwidth on a common communications medium. With this basis, contention-based access is nondeterministic since stations cannot be guaranteed bandwidth resulting in unpredictable communications. CSMA/CD also specifies half-duplex communications since only one device can place data on the medium at any given time. Consistent with the linear bus’s technology, every node necessarily sees all frames since all devices must parse and inspect each frame to determine if they are the destination.
A linear bus topology that implements contention-based access results in a logical collision domain as the device’s transmissions will inevitably collide and become corrupted. Corrupted transmissions resulting from collisions degrade throughput and require recovery mechanisms further decreasing available bandwidth. To put this in perspective, consider that 40% to 50% of a network’s available bandwidth can be consumed by collision recovery in a moderate-sized CSMA/CD Ethernet network. Additionally, consider that a network that contains broadcast traffic in excess of 10% can incur significant network delays. While inevitable, these data collisions may be considered to be the result of Ethernet’s simple and low implementation costs and overhead. With this basis, it is obvious the data link layer must provide mechanisms to manage transmissions, reduce collisions, and resolve contention. Two common protocols exist to manage a shared contention-based environment, CSMA/CD for IEEE 802.3 Ethernet networks and Carrier Sense, Multiple Access with Collision Avoidance (CSMA/CA) for IEEE 802.11 wireless networks.
CSMA/CD
As introduced above, Ethernet specifies a multiple-access architecture where all devices have equal or non-prioritized access to a shared and contention-based communications medium. This results in a communications collision domain and necessitates physical specifications and additional protocols to manage, constrain, and resolve communications. These physical specifications include maximum line lengths and limits on the network’s number of intermediary devices. It should be noted these physical specifications and intermediary devices depend on the type of physical communications medium. As cited above, a multiple-access contention-based environment creates the need for additional protocols to ensure reliable communications. Ethernet and CSMA/CD contain best-effort protocols to manage medium access through Carrier Sensing (CS) and provide mechanisms for Collision Detection (CD) and Collision Recovery (CR).
To frame the following analysis, the CSMA/CD protocols are introduced in the following use-case Ethernet communications example followed by individual analysis of the Ethernet’s CS, CD, CR, and timing mechanisms followed by Ethernet’s limitations. In an Ethernet 802.3 LAN, a computer listens to network media through its Network Interface Card (NIC). In this scenario, the signal is known as the carrier. If the media is busy (i.e. there is a carrier on the medium), the device waits until the media is free of transmissions to transmit. If the media is idle, (e.g. no carrier) the computer sends its data immediately. Following the transmission, all computers on the network wait 9.6 seconds to allow each device to process the frame after which they again compete for media availability. It is possible that two devices will concurrently perform a carrier sense, find the media available, and begin to transmit resulting in a collision. In this case, the devices must detect the collision and upon detection, generate a jam signal that notifies all devices of the corrupt frame. Following the jamming signal, the devices wait a random back-off period prior to returning to a carrier sense mode in an attempt to retransmit.
Carrier Sense (CS)
The first step in a device’s attempt to avoid collisions is to perform a carrier sense. Recall that Ethernet is not only multi-access from a transmissions standpoint but all stations continually read each frame to determine if they are the frame’s destination. With this basis, each station is continually performing a CS through its Network Interface Card (NIC). A NIC is a printed circuit board that provides an interface between the computer and the network. The NIC communicates with the computer through a parallel communications bus and communicates with the Ethernet backbone through a serial bus.
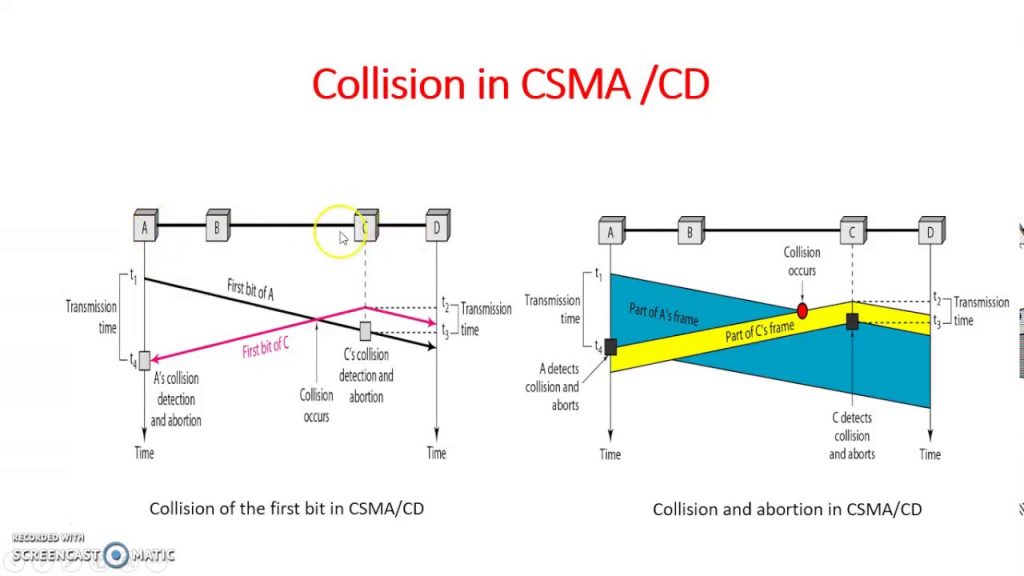
Collision Detection (CD)
The NIC is responsible for detecting collisions by comparing its generated signal with the physical medium’s state. A collision occurs when two or more devices sense an idle media and begin transmitting unaware that the other device has begun to transmit. If a collision has occurred, the signals will corrupt each other and the communication medium’s state will be different from what the station is transmitting. Note this also identifies a possible point of catastrophic failure as a faulty NIC on a traditional CSMA/CD backbone could continually transmit without regard to the CS and CD protocols.
Collision Recovery (CR)
When transmitting devices detect a collision, they transmit a jam signal for a predetermined time to alert all devices on the logical segment the frame has been corrupted and wait a random back-off period before attempting to retransmit. Most commonly the jam signal is a 32-bit repeating pattern of ones and zeroes similar to the preamble. Upon detecting a jam signal, all devices transmitting or seeking to transmit invoke their own random back-off algorithm. If a station fails to transmit after 16 attempts, the MAC layer gives up and returns an error message back up to the network layer.
Ethernet CSMA/CD Constraints
Ethernet CSMA/CD Timing Constraints
Collision detection and subsequent jam signal generation impose constraints on LAN design as stations must detect the corrupted signal and broadcast a jam signal before they finish transmitting. This ensures that all devices receive the frame before the transmitting NIC has finished transmission. The smallest permissible Ethernet frame is 64 octets (i.e. 64 bytes) therefore collisions must be detected within the first 64 octets of transmission. CD and subsequent generation of a 32-bit jam signal curtails transmission prior to the generation of a minimally sized Ethernet frame resulting in a runt frame. Run time frames fail Ethernet’s minimum length and FCS tests and are therefore discarded by devices with minimal processing overhead.
A station’s random back-off timing is measured in intervals of slot frame length that is in turn dependent on the network’s design and physical characteristics. Recall that to properly send a jam signal, a device must determine a collision has occurred before it completes the transmission of a minimal-sized frame. To provide an adequate temporal buffer, the slot time is defined to be equal to twice the time it takes a signal to travel between the two most distant stations on the network. It is obvious that collisions could be detected in half this time however this extra delay accommodates inter-frame spacing that allows signals to dissipate after successful transmission. With this basis, the network’s physical medium’s characteristics and topology determine the slot time, inter-frame spacing, and physical segment lengths.
Ethernet CSMA/CD Physical and Logical Constraints
Ethernet and CSMA/CD have both physical and logical network segment constraints. From a physical medium standpoint, transmissions can only travel limited distances since line noise and signal attenuation continually degrades the signal. This transmission limitation can be overcome through the use of layer one repeaters or hubs allowing more devices to access the shared media and allowing data to be transmitted over longer distances. Hubs and repeaters receive and retransmit transmission signals increasing network latency. Layer one devices do not parse or interpret information and therefore cannot segment the logical CSMA/CD collision domain. Also, note that a hub does not terminate an Ethernet LAN, therefore, signal dissipation and inter-frame spacing remain unchanged. Extending an Ethernet LAN with layer one devices can in fact decrease throughput as additional devices increase contention for the shared media and slot times may need to be lengthened due to increased geographical separation.
As cited in previous coursework, linear bus topologies are prone to a single point of failure. This can be partially overcome through the use of layer one hubs to create a physical tree topology however this does not logically segment the collision domain. Logical collision domains do not scale well with the increased number of devices, frequency transmissions, increased loads or increased cable distances between devices as these all result in a higher incidence of collisions. Note that an increasing number of collisions results in an increased number of retransmissions and may create a cycle of unresolved network congestion.
When implementing a tree topology, network designers are advised to adhere to the de facto industry standard “5-4-3” rule that provides constraints on the network’s layout. Recall that intermediary network devices incur transmission propagation latencies that affect the collision domain’s CD. The “5-4-3” rule states that a network should be constrained to never permit the separation of any two nodes on a network by more than five network segments, four repeaters, or three backbone segments. This general rule of thumb constrains the network’s propagation latency to acceptable levels allowing network designers to implement systems without calculating and configuring the network’s exact timing requirements (e.g. slot time, inter-frame spacing, etc.).
The Evolution and Future of Ethernet
As previously cited, network architectures must be designed to appropriately balance the organizational and end device’s needs and these considerations include: (a) the data rate, (b) the cost of the components, their installation, and their maintenance, (c) the necessary fault tolerance, (d) the network’s scalability, (e) Quality of Service (QOS), (f) security, and (g) availability. These considerations have a direct correlation with the choice of the network medial, network topology, and its access methods. The Ethernet standard has been continually updated to add more capabilities and functionality to support emergent organizational needs. Today’s large networks typically include a large number of end systems, servers, and network devices and support a hierarchy of Ethernet connectivity in terms of topologies and mediums.
Ethernet has evolved to support full-duplex functionality without the need to install new media. This full-duplex functionality is achieved through point-to-point links between layer two switches and end nodes that overcome the shortcomings of legacy CSMA/CD collision domains. Simply upgrading to Fast Ethernet can significantly improve throughput and diminish the consequences of a CSMA/CD network since network latency is decreased. This decreased propagation time allows stations to avoid and detect collisions earlier in the transmission process. Note that upgrading from a legacy Ethernet implementation to today’s faster Ethernet standards will incur a substantial cost as NICs and intermediary devices will need to be replaced. Most Ethernet, Fast Ethernet and Gigabit Ethernet NICs sold today now support full-duplex mode with the NIC CD circuit necessarily disabled. The introduction of fiber-optic Gigabit Ethernet has extended LAN’s geographical distance to accommodate Metropolitan Area Networks (MAN) and provides the requisite infrastructure for today’s converged communications. With this basis and in accord with its original design tenets, Ethernet continues to be an easily maintained, reliable and low-cost communications technology capable of supporting new and unforeseen technologies.
CSMA/CA
WiFi is CSMA/CA (collision Avoidance) which is similar to Ethernet (i.e. CSMA) but differs by transmitting a request to transmit prior to transmitting and transmits when it receives permission.
| Sr. No. | Key | CSMA/CA | CSMA/CD |
|---|---|---|---|
| 1 | Effectiveness | CSMA/CA is effective before a collision. | CSMA/CD is effective after a collision. |
| 2 | Network Type | CSMA/CA is generally used in wireless networks. | CSMA/CD is generally used in wired networks. |
| 3 | Recovery Time | CSMA/CA minimizes the risk of collision. | CSMA/CD reduces recovery time. |
| 4 | Conflict Management | CSMA/CA initially transmits the intent to send the data, once an acknowledgment is received, the sender sends the data. | CSMA/CD resends the data frame in case a conflict occurs during transmission. |
| 5 | IEEE Standards | CSMA/CA is part of the IEEE 802.11 standard. | CSMA/CD is part of the IEEE 802.3 standard. |
| 6 | Efficiency | CSMA/CA is similar in efficiency as CSMA. | CSMA/CD is more efficient than CSMA. |
References
5-4-3 rule (2009). Pcmag.com encyclopedia. Retrieved April 9, 2009, from http://www.pcmag.com/encyclopedia_term/0,2542,t=5-4-3+rule&i=37141,00.asp#
Cannon, K., Caudle, K., & Chiarella, A. (2009). CCNA: Guide to Cisco networking (4th ed.). Boston, MA: Course Technology
Comer, D. E. (2000). Internetworking with TCP/IP: Principles, protocols and architectures, (4th ed.). Upper Saddle River, NY: Pearson Publishing.
Dye, M. A., McDonald, R., & Rufi, A. W. (2008). Network fundamentals: CCNA exploration companion guide. Indianapolis, IN: Cisco Press
IEEE 802. (2009). IEEE standards association: IEEE 802.3 LAN/MAN CSMA/CD access method, Retrieved April 8, 2009, from http://standards.ieee.org/getieee802/802.3.html
McQuerry, S. (2008). CCNA Self-Study: Introduction to Cisco networking technologies Part 1 (ICND1) 640-822 (2nd ed.). Indianapolis, IN: Cisco Press.
Odom, W. (2003). CCNA INTRO exam certification guide (CCNA Self-Study, 640-821, 640-801), (1st ed.). Indianapolis, IN: Cisco Press