First, a nice introduction of our present environment. Please note the well developed and networked business side of this malware. Note the effective social engineering and need to properly train all employees in security and again, in accord with the Systems Development Life Cycle (SDLC), training is pure overhead as employees in training are not performing mission work. It is very apparent that we need to understand command line OS knowledge. You will also see an injection attack and we will understand this much better than the general audience member since we understand the 3-tier Web architecture (i.e. Web server, middle tier business logic which passes the SQL injection code through to the core DB tier).
Towards the end of the presentation, please recall my statement that security is 75% policy and how I can’t trust anything my family and friends send me via email. I cannot manage their security and it would be very bad if the Dept Chair of Computing and Information Sciences was to catch and spread malware… this is now extended to social networking and even social engineering. Finally he concludes with the statement I presented on day 1, “Fewer and fewer people know how to or are interested in looking under the hood of computing”.
Cyber Espionage
Mobile Malware (and Use Policies)
In class, I always ask who has read the HVCC Computer Use Policy and it is rare that anyone has read it. This is important on many levels. First, it serves as professional development since it is likely that you will be asked to create or review policies in the future. Second, computer use and privacy policies are important for your protection and on this note, how many of you have read the Facebook and/or Google privacy policies. To really drive home the need to do this requisite research please see the following especially if you are an Android user.
The lesson is, always be on guard and always read the use and privacy statements.
Anatomy of Phone Theft/Hijack
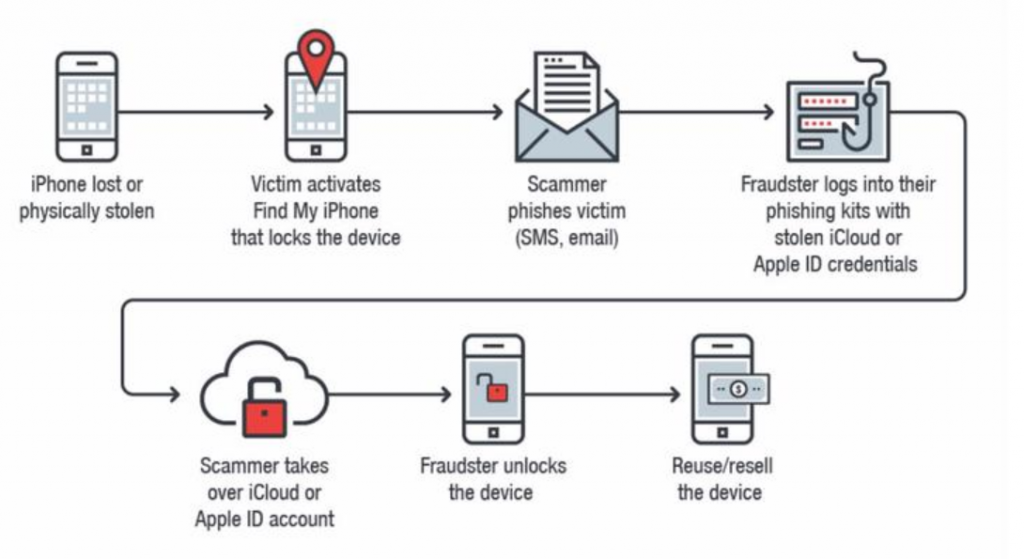
Business Discussion
Now we need to discuss this on another level (recall Business-IT-Society triangle). Recall our definition of architecture. If you are a CIO and you are allowing or deploying mobile devices what platform (e.g. Apple or Android) would you choose? Apple is expensive but as previously introduced, the iTunes store serves as a gatekeeper largely keeping malware off the ios platform so employees downloading apps from iTunes represents minimal risk. In contrast, if you purchase Android phones for your employees, they will download and install their own apps and the looser freer Android App Store approval and distribution process creates a far riskier environment.
Cybercrime
Now have you ever thought about what it would take to take advantage of 1 million stolen credit cards? A single person cannot use 1 million stolen cards as they would be discovered very quickly. Extending this, 100 or even 1000 or even 10,000 people could still not leverage or take advantage of 1 million stolen credit cards as even in the last case each one of the 10,000 people would need to use 100 credit cards and they would likely be discovered. What this illustrates is that you need a extremely large network of bad people to take advantage of 1 million stolen credit cards so in other words => Organized Crime.
Now it is also recognized that 1 genius hacker is worth 100s or 1000s of good programmers. Recruiting and paying a genius hacker a good salary is not difficult and provides a good return on investment. As an example, consider if you were a gifted programmer graduating from a top school. You are offered a job doing what appears to be legitimate work for ~$200,000+/year. Would you take the job? What is the ROI for organized crime paying a genius programmer this salary for several years when the payoff could be millions of stolen credit cards?
What I really wanted to drive home with this example is while everyone acknowledges computer crime, we have to look deeper at the business model as well (Business-IT-Society).
Phishing
Please see the submenu for examples.